Set up and configure an identification and access administration system: When you don’t have one by now, set up and configure an identity and access administration system (IAM). This is when the policies are going to be described, resources classified and buyers assigned permissions.
The principal of minimum privilege is the greatest exercise when assigning legal rights within an access control system. The entity is only offered access to your means it requires to carry out its immediate job capabilities.
You'll find differing kinds of access control and a corporation's choice usually hinges on variables like its dimensions, IT assets at its disposal (both equally expertise, and infrastructure), and its security demands.
To beat these troubles, corporations are ever more adopting centralized id administration alternatives. These remedies provide a unified see of user identities and access rights across all systems and purposes.
You are able to email the site operator to allow them to know you were being blocked. Be sure to involve Anything you ended up executing when this site arrived up plus the Cloudflare Ray ID located at the bottom of the page.
Within an ACL-primarily based design, a subject's access to an object relies on whether or not its identity seems on an inventory affiliated with the article (about analogous to how a bouncer at A personal bash would Look at an ID to see if a reputation appears within the guest record); access is conveyed by modifying the checklist.
Physical access control is a matter of who, where, and when. An access control system determines that's permitted to enter or exit, where by They are really permitted to exit or enter, and when they're permitted to enter or exit. Historically, this was partly achieved through keys and locks. Any time a door is locked, only somebody using a key can enter from the door, based upon how the lock is configured.
Compared to other ways like RBAC or ABAC, the main variation is that in GBAC access rights are outlined applying an organizational query language as an alternative to full enumeration.
Access to an enormous library of self-enable resources and also the LastPass Local community, that is actively monitored by LastPass professionals.
Personnel who unintentionally or intentionally mishandle qualifications pose a significant risk to your small business. Password administration alternatives help mitigate this chance by limiting access and checking consumer pursuits.
Improperly managed user access, In particular during staff onboarding and offboarding, can result in unauthorized access and details publicity.
Virtual Non-public Networks are one of the most commonly utilized methods to apply access controls. This allows end users to securely access resources remotely, which happens to be significant when Performing away from the particular workplace. VPNs may be used by firms to offer Safe and sound access to their networks when staff are spread out around the world.
Not like DAC systems, access selections are certainly not still left on the discretion of particular person source entrepreneurs. Instead, They're centrally managed by an authority, usually an IT admin, based on predefined stability policies – rules and recommendations established by a corporation to classify facts and control access.
How to produce a personalized Windows eleven graphic with Hyper-V When directors can system access control deploy Windows systems in many ways, making a customized VM with Hyper-V permits them to successfully deploy...
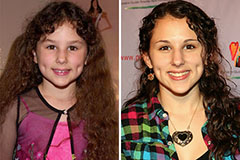 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Josh Saviano Then & Now!
Josh Saviano Then & Now!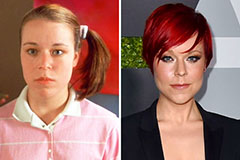 Tina Majorino Then & Now!
Tina Majorino Then & Now! Kerri Strug Then & Now!
Kerri Strug Then & Now! Sarah Michelle Gellar Then & Now!
Sarah Michelle Gellar Then & Now!